Network security company ESET recently discovered a new type of macOS malware, CloudMensis. Once a Mac device is infected, it will be implanted with a backdoor, infiltrating the local network, recording keystrokes, viewing files and screenshots, and stealing important and sensitive information. The malware can even recover deleted emails, attachments and related files.
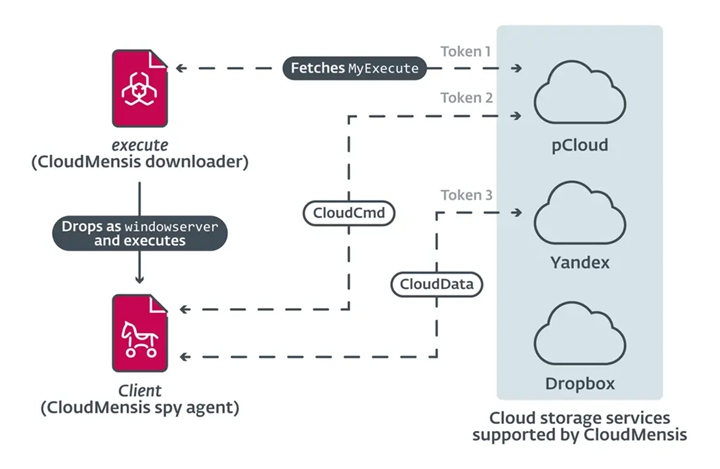
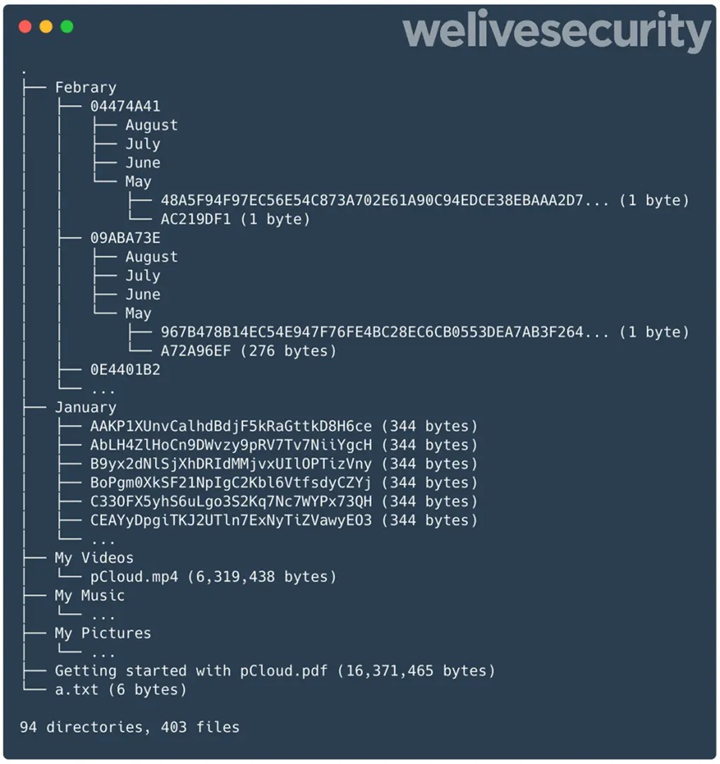
CloudMensis malware uploads this data to public cloud storage systems like pCloud, Yandex Disk, and Dropbox for subsequent use by attackers. ESET found that these uploaded files were automatically sorted by month and victim name.
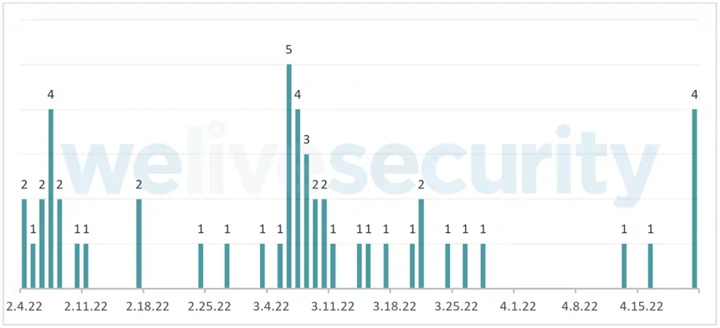
The first Mac devices attacked by CloudMensis date back to February 4, 2022, suggesting that this is a new type of malware targeting Mac devices. The malware has not yet spread widely, but their goals are clear.
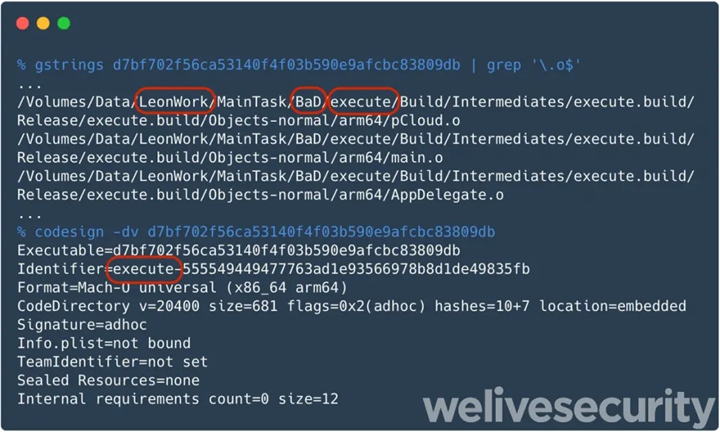
The current investigation shows that the malware did not use a zero-day exploit, but a previously exposed vulnerability to bypass the protection of macOS. So Mac users can protect themselves from the malware by upgrading to the latest version.
Once a device is infected with CloudMensis, it attempts to execute code to gain system administrator permissions. The malware then enters its second stage, where CloudMensis executes around 39 commands to collect data on infected devices.
Researcher Marc-Etienne Leveille said: “At the moment, we don’t know how CloudMensis spread in the early days, nor its main targets. However, the quality of the code and the lack of fuzzing suggest that the malware’s developers did not Not familiar with Mac development and not a seasoned Mac developer.”
