The computer was attacked by a ransomware virus, but the hacker did not ask to pay the ransom, but instead demanded to do a good deed to unlock the computer. Have you ever seen such an alternative virus?
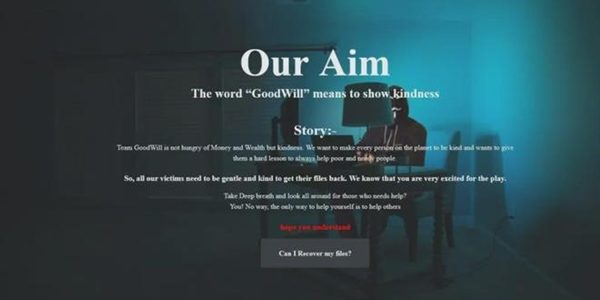
Recently, CloudSEK’s threat intelligence research team recently discovered a ransomware called “GoodWill”. If the victim wants to obtain the key, he must do something good: provide food, blankets to the unfortunate, or donate money to the sick , can only be unlocked after completing these three “good things”.

The first request was to provide clothes and blankets for those in need by the roadside and to videotape themselves doing so. The film must also be posted on social media to encourage others. Finally, this information must be emailed to the attacker as proof of completion.


The second requirement was to find 5 poor kids under 13, take them to a fast food restaurant, and make them happy. Victims also had to take selfies with the children and post photos and videos on social media. Finally, a photo of the restaurant bill along with a link to a social media post had to be sent to the attacker.


The third requirement is to go to the hospital to pay for medical bills for those in need of financial assistance. Of course, it is also necessary to take selfies with the recipients and record audio conversations as evidence. Then, a “beautiful article” about the matter had to be posted on social media, explaining to people how the GoodWill ransomware made themselves a more loving person.


When all three requirements are fulfilled, the attacker sends a decryption tool, which then unlocks the archive data.
In addition, CloudSEK was able to trace IP addresses and e-mail addresses back to an IT company in India that allegedly managed end-to-end security, but there is no definitive answer as to which group produced and operated the ransomware.


source
Further reading: